Swiss Infosec AG supports you in testing and improving the security of your IT infrastructure. A dedicated team of IT security specialists and penetration testers supports you with a wide range of consulting services and training courses on IT security.
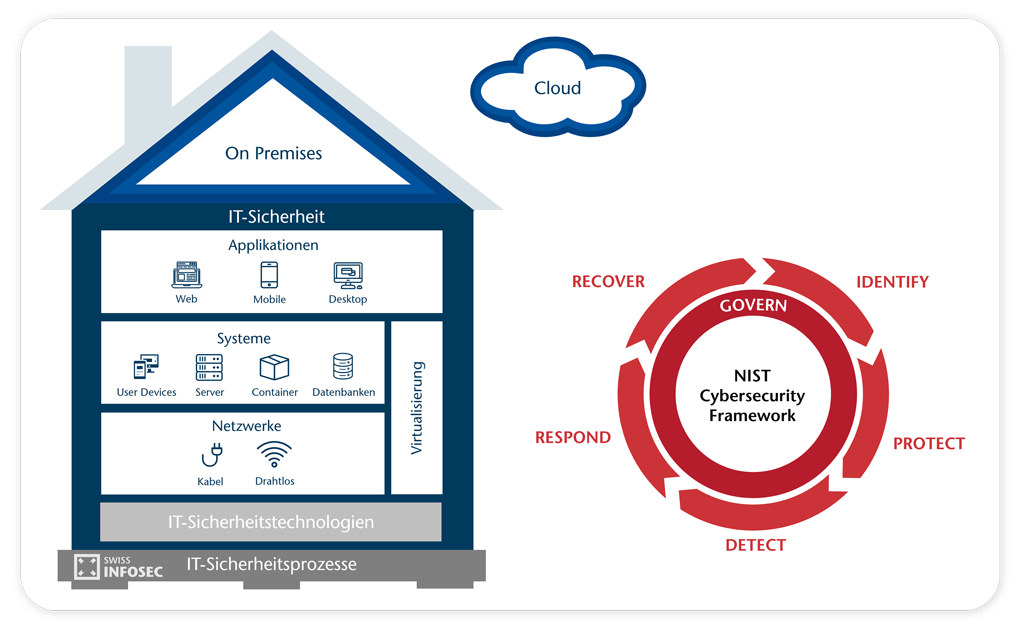 Infografik IT-Sicherheit
Infografik IT-Sicherheit

Penetration Test
Take advantage of the expertise of Swiss Infosec AG’s penetration testers to carry out an attack simulation to test the resilience of your systems. Swiss Infosec AG’s penetration testers use the same tools, techniques and procedures (TTP) that would be used in a real attack. Get more information about:


Red Teaming
Check the effectiveness of your existing organisational and technical defences by letting us simulate real attack scenarios for you. This allows you to test, train and strengthen your security organisation and increase your organisation’s resilience against cyber attacks.


Software Security
Do you want to check and sustainably improve the security level of your software products? Whether high-level analysis of software design and architecture or low-level analysis of source code: we offer individual software security reviews tailored to your requirements.


Darknet Exposure Reporting
Early identification of leaks and breaches in the darknet, deep web and relevant criminal forums provides an understanding of your company’s exposure in relevant areas of the internet and can also be used as an early warning system for attempted attacks. Our service enables you to identify risks such as identity theft, reputational damage or targeted attacks in good time and to take proactive countermeasures.


Legislation and regulatory requirements
The threat posed by cybercrime and cyber warfare is increasingly being addressed by legislators and supervisory authorities with appropriate legal and regulatory requirements. With our combination of legal, technical and organisational expertise, we support you in addressing the applicable requirements in a practical and appropriate manner.
- FINMA circular 2023/1: Operational risks and resilience
- Information security law of the Federation (ISL)
- Digital Operational Resilience Act (DORA)
- EU directive Network and Information Security (NIS2)
- Cyber security and data protection laws of the People’s Republic of China


Cloud Services Security & Compliance
Although the use of cloud services can offer many advantages, it also regularly causes headaches for those responsible for security and compliance. The additional complexity in terms of technical architecture, legal requirements and organisational challenges is anything but trivial to deal with. We would be happy to support you with the challenges ahead.
- Hardening checks & cloud security posture management
- IT provider assessments
- Microsoft Cloud Security & Compliance


IT security processes and concepts
IT security audits are only snapshots and do not guarantee sustainable IT security for your organisation. We would be happy to support you at the conceptual level in establishing suitable and pragmatic IT security processes or in developing specific IT security concepts. Get more information about:


Training and awareness
Around half of all cyber attacks succeed due to human error. We are happy to support you with various methods to raise your employees’ awareness of IT security issues. Get more information about: